Although the cloud is becoming more and more popular in Poland, moving into it is still quite a challenge for many Polish entrepreneurs. The following guidebook is for those who still hesitate or wonder if it is worth doing, or have no idea how to prepare for it.
The cloud – solution of the XXI century
Cloud is a modern IT environment that answers the need for flexible business support. It provides a configurable resource shared with various entities in order to launch IT business solutions dedicated to them, separated from other cloud users. Cloud services may be delivered using different models, the most popular ones include: IaaS: Infrastructure as a service, PaaS: Platform as a service, SaaS: Software as service, the remaining two, less popular, are: MBaaS: Mobile “backend” as a service and FaaS: Function as a service.
Nowadays, the cloud has been commonly identified with public solutions where many companies share the resource with access via the Internet, and this solution shall be discussed in the further part of the article. However, it should be kept in mind that there are also private hybrid solutions.
Year by year, more Polish companies decide to use various options for cloud services. What convinces them to do it are, most of all, no need for investing in their own infrastructure, easy scalability and flexible use. The price of cloud services is rarely an obstacle in making the decision to switch into them.
The main problem and barrier for the unconvinced is the concern about security, especially about data loss or leakage. Ironically, especially in the case of small and medium-sized companies, migration to cloud may be safer than the solutions installed in local server rooms.
The concerns are much exaggerated
A good cloud is, among all, a location secured against unauthorized access, 24h infrastructure monitoring, protection against DDoS attacks, environment updates, backups, a team of qualified specialists, etc.
Nevertheless, we need to remember that transition to the cloud does not mean moving the responsibility for the security of the provider.
Using cloud does not relieve us from this responsibility but allows to move part of the tasks concerning security onto the provider. It is crucial to be fully aware of the provider’s obligations and to ensure completing the remaining tasks. This allows to avoid the so-called grey area which nobody cares about, and this makes it the weakest link and first thing to threat the security.
Devil is in the detail
Task division depends on the type of services we use. The below-presented figure presents the standard share of responsibilities, as for used services:
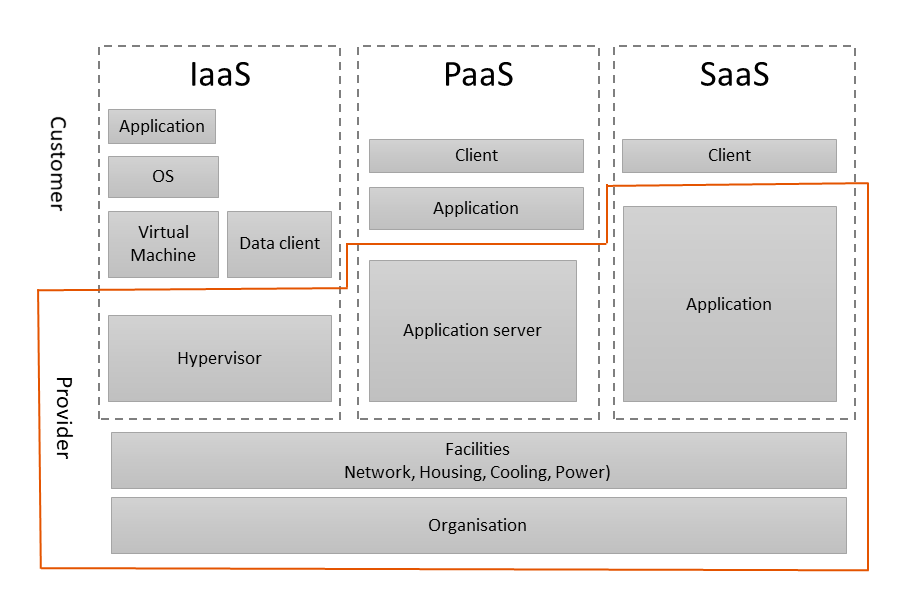
Based on ENISA materials
When we move the server contents to the cloud from a service room (IaaS service), the provider is the party responsible for physical security, power, air conditioning or network. Still, the responsibility for security of many components comprising our solution, such as for instance operating the system, database, application, data or access to the solution is on our side. If we decide to use CRM as SaaS service instead of moving it into the cloud, our liability limits to managing the access to the application. With the decrease in our responsibility, the number of tasks we gave away to the provider increases, as illustrated below:
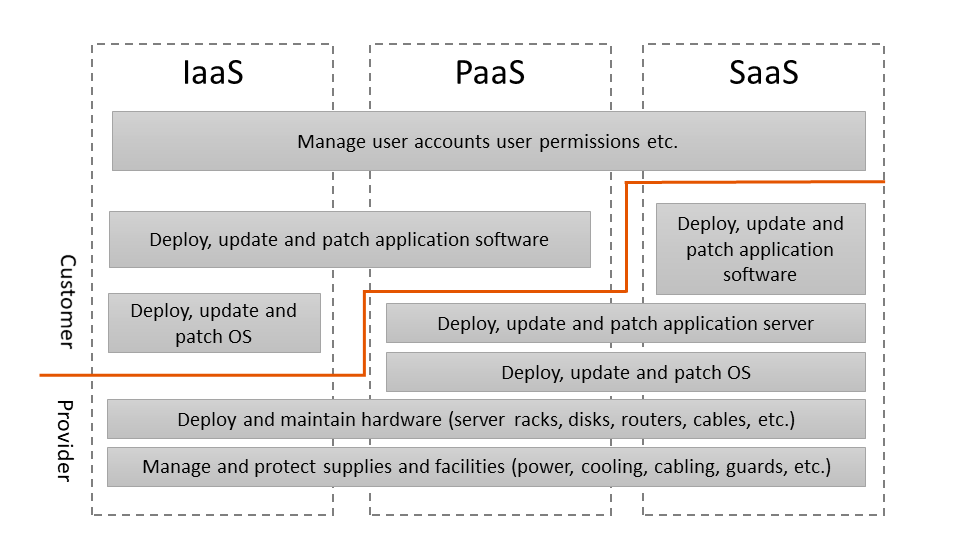
Based on ENISA materials
In every case, no matter which services are in question or what is the task division, security involves availability assurance, data confidentiality, and integrity, where:
- availability – stands for the possibility to use company resources on the basis of rules preserving the continuity of operation;
- confidentiality – preventing access by unauthorized individuals or systems;
- integrity – certainty that the data was not unlawfully altered.
If you need a security audit, contact our expert.
Make a conscious choice
Before you make the decision to use the cloud:
- Analyze the current situation of the company, type of processed data, check whether there are any limitations (e.g. resulting from RODO).
Consider whether you want to move the entire IT environment or to use hybrid solutions (to move only part of the resources). Also, it is good to identify the people with access to the resources, verify their personal data and current privileges. Many companies make necessary authorizations but hardly ever makes sure the workers still have them even after they are no longer needed. Minimum and only necessary authorization is one of the key issues in security. - Determine which services (IaaS, PaaS, SaaS) you need. What needs to be developed from scratch and what can be replaced, e.g. with SaaS services (CRM system, circulation of documents, etc.);
- Plan security mechanisms, including:
- the above-mentioned rule for minimum and necessary privileges;
- work based on roles, e.g. to avoid the common practice of connecting user’s and administrator’s privileges on a single account;
- MFA (Multi-factor authentication ) implementation, functionality that forces the user to provide extra identity authentication, apart form login and password. It may be, for instance, using an extra USB key, or retyping the code sent to the user’s mobile phone.
All these mechanisms are well-known and commonly used within an on-premises infrastructure where it is often possible to access the resources only within the network. Therefore, it is even more important to remember about them in terms of cloud solutions where access is possible everywhere via Internet connection.
Along with the reduction of wide access to the services it is worth implementing other mechanisms such as allowed devises, locations or login time, and many more.
Moreover:
- Make sure the data is properly secured when at rest. Most service providers store data in a disturbing form, encrypted using their own keys. If it is too little, check if you can use your own keys (it requires further management), or put the highly sensitive data already encrypted in the cloud.
- Data sent between the users, business partners should be transferred as encrypted files, via e-mail or dedicated links which requires identity authentication.
- Determine how many and which cloud services you need and provide a list of service providers that are able to provide them.
- Choose the provider, check at least:
- Does he support solution development and migration?
- How can you increase or decrease your need for resources? What is the change duration tame?
- Where will your data be stored? It is especially important in terms of RODO. Sometimes, depending on the services, one provider stores data in various locations, also outside the EU.
- How does the provider care about security? Does he have a security policy, allow for internal audits, present reports drafted by independent auditors? Does he have security certificates issued by independent organizations such as ISO/IEC 27017?
- Does the provider allow to monitor the used services? On what level?
- Is there a notification process for users informing them about failures and scheduled works? If and how you can influence the time of scheduled works?
- How can you report problems and whether the operator guarantees the time of taking the notification and solving the problem (SLA)?
- How often and how is backup made? What does the process of restoring the data look like? When dealing with highly sensitive or significant in terms of business data it is good to verify if there is a possibility to export it to an external system, e.g. at another could provider.
- Sometimes it is necessary to resign from the used cloud. It may happen due to various reasons, such as provider’s downfall, lack of newly required functionalities, or prices inadequate to the market level. Such a situation requires checking whether the provider offers data access via standardized interfaces, stored in known formats. Alternatively, if he ensures tools allowing data conversion. The lack of such mechanisms may lead to Vendor Locking which prolongs the time and increases the effort and cost of the solution which surpasses the benefits.
- Think if your organization has enough competence to choose the best services for your needs, plan the architecture and conduct migration, and then to provide maintenance. If not, employ specialists or provide your workers engaged in the project with appropriate training, or find a reliable and experienced partner.
- Plan migration. In what order and what should be moved? Start with less critical resources form the business point of view.
- Prepare internal communication in the company. Projects concerning migrating data to the cloud very often set not only technological or operational challenges but also require facing the lack of acceptation or negation from prospective recipients. This is a natural reacting for changes. In order to mitigate the resulting risks, you should:
- Prepare a detailed communication plan involving all people and collecting feedback. It will allow for a fast reaction when problems occur, to adjust actions to the current situation, plus, it will increase the engagement and co-responsibility for the project among the workers.
- Prepare and pass knowledge about new solutions for future users and administrators.
- Plan the support for users after solution launching.
- If your users intend to work in a crowded space, make sure the Internet connection is fast enough. After data migration, the slow connection often becomes a bottleneck.
- Evaluate risks. Moving into the cloud environment may cause extra risks, new for the own infrastructure. It is required to conduct an analysis of the new threats, classify them in terms of occurrence probability and their influence on business activity. Next, you need to plan and implement mechanisms that will allow to monitor them. It is good to get acquainted with the provider’s offer who very often provides necessary tools.
- Update or create a security policy and make sure that users know it and understand it.
No more or no less?
A defined aim, a good plan, a set division of duties, proper execution, and we are safe in the cloud. It seems like a perfect time to relax. Not at all. Security is not a state that can be reached once and forever. It is a constant process: following the changes everywhere around, monitoring threats, preparing to prevent them, verifying security efficiency, fixing vulnerabilities and continuing to follow the changes. It is a never-ending work, no matter if we use our own resources of the cloud.
More about our offer of audits and security testing.
Written by Marcin Szydłowski, CITO, Soflab Technology Sp. z o.o.
Fotografia Philipp Birmes / Pexels